In 2023, the world witnessed some of the most consequential cybersecurity incidents in modern history, and the 2024 picture certainly isn’t looking any brighter – it’s predicted to be “2023 on steroids” by the Wall Street Journal. It’s an ominous warning that the rate and intensity of cyberattacks on individuals and organizations are likely to get worse in the days ahead.
Threat actors motivated by geopolitical, financial, and other reasons will continue to attack personal, business, and governmental information day after day with the goal of upending people’s lives, stealing secrets, and disrupting society.
As services continue to advance, video conferencing information is growing in importance and value. Since Covid-19, the world has made video conferencing mainstream, moving it from the category of ‘once in a while’ to simply ‘the way work is done’. It’s a development that has opened the door for vast communication and collaboration opportunities – along with a host of new security threats.
The solution to this global challenge is neither regression nor abstinence.
Instead, we must explore the right methods and technologies to reduce the risk of unauthorized access to, and information leakage from, our private virtual meeting spaces. Threat actors have progressed far beyond the days when a password was sufficient in thwarting the attack.
According to Gartner’s Market Guide for User Authentication, organizations are in hot pursuit of more advanced and robust security measures. Increasing attacks against “incumbent multifactor authentication methods” are moving clients towards new methods such as “phishing-resistant MFA” and “robust identity verification”. Pexip also sees a growing need among video conferencing users to be able to define the nature of the meeting, assess the risk or impact level of that discussion, and then implement the appropriate controls and protections required for that meeting. Because not all meetings require the same protections.
So, how do you determine the right security measures for your meetings? That’s where Pexip can help.
We’ve prepared an easy overview showing which security capabilities are recommended for specific types of meetings.
Security hierarchy for your video meetings
Low risk
Low risk video meetings are your everyday video calls to your grandmother or a good friend. They are informal and often of a personal nature, with conversations on everything from the weather in Boston, to your recent trip to Portugal, to how your favorite sports team is faring.
Security recommendations for “low risk” video meetings:
- Deployment: Traditional Software-as-a-Service (SaaS) video solutions are sufficient for these types of meetings.
- Authentication: The standard security measures for your personal video meeting account typically include password protection. No additional security measures are necessary for these low risk meetings.
Limited risk
Limited risk video meetings are typically the general business meetings in which no confidential information is exchanged. This may include a team meeting, a short catch-up between people, or a discussion of everyday matters in the workplace.
Security recommendations for “limited risk” video meetings:
- Deployment: Traditional Software-as-a-Service (SaaS) video solutions are sufficient for these types of meetings.
- Authentication: A step up from low risk meetings, the limited risk meetings should offer one-time meeting links (to prevent threat actors from guessing the link), PIN code access to the meeting, as well as single sign-on to the meeting, to ensure that the right people are in attendance.
High risk
High risk video meetings are meetings in which confidential or private information is exchanged. This typically takes place in government, finance, healthcare, legal and other large corporate organizations and is usually governed by either organizational or statutory data protection rules.
These meetings are deemed high risk due to the nature of the discussions involved, which might be trade secrets, business strategies, personally identifiable information (PII), protected health information (PHI), or similar types of information.
Security recommendations for “high risk” video meetings:
- Deployment: For high risk meetings, more control is needed over where your data is stored, who has access to it, and where it travels. Securing this level of control requires a private cloud or on-premises hosted solution, rather than a traditional SaaS deployment.
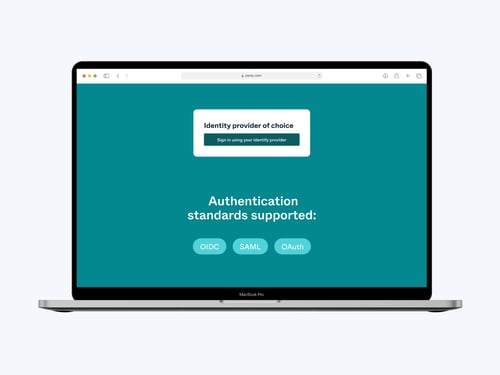
- Authentication: The authentication measures get stricter for high risk meetings. In addition to basic methods like PIN code and single sign-on, two-factor authentication is recommended, plus a policy engine that gives the organization role-based and attribute-based access control (RBAC and ABAC, respectively) over how network resources and organizational data can be used and accessed. For example, if you are in the military, you could limit access to a certain rank.
Unacceptable risk
Unacceptable risk video meetings are meetings at the highest security level, in which risks to security could be catastrophic in impact. This may include government officials, intelligence agencies, military/defence organizations, and similar – meetings that must remain confidential at all costs. Simply put, it would be unacceptable if any information were to leak.
Security recommendations for “unacceptable risk” video meetings:
- Deployment: Full control and privacy are critical for these types of ultra-confidential meetings. For unacceptable meetings, deployment should be in a private cloud, on-premises, or air-gapped for complete isolation from outside threats.
- Authentication: More authentication is required for these types of meetings. A policy engine is recommended, plus two factor authentication, and biometric authentication through fingerprint or facial recognition. External identity providers are also suggested as an extra layer of verification for the participants.
Learn more here about how Pexip can help protect your video meetings from unauthorized access.
- Meet & collaborate securely
- Secure Meetings
- Secure Collaboration



.jpg?width=500&name=policy%20server%203%20(1).jpg)
.jpg?width=500&name=blog%20(3).jpg)